This article describes ways to secure Web applications built using map.apps and security.manager. map.apps alone offers a number of security features that may be sufficient for simple applications. Combined with security.manager, almost all requirements for safety are met. It is possible to configure extremely fine-grained access protection for both services, as well as functions of map.apps Apps.
Security with map.appsManage and release apps
Apps for map.apps are created and managed in map.apps Manager. By default, there are three types of users who differ in their rights when configuring Apps.
- The Administrator user has full access to all apps and may create, configure and delete apps.
- The editor-user can configure and enable or disable existing apps, but is not permitted to create or delete them.
- Anonymous users who have not logged on with a username and password can access and use apps, but have no configuration rights.
The administrator and the editor users may use the map.apps Manager, to define what stage of their life cycle an app is currently at. For example, an app can be at the stage of "design", "Approved" or "Archived". Only apps in the "Released" phase are visible and accessible by anonymous users in the App Launcher.
Securing apps
In map.apps there is the possibility to use the map.apps Manager to assign permissions for launching apps to certain user roles. This requires map.apps to be coupled to an external user directory, such as security.manager or ArcGIS Online. It can then be determined which user roles may run each individual app.
Role-based app protection with help from security.manager
The Administrator, as well as the Editor-user, are predefined users in the standard delivery of map.apps. As an alternative, security.manager may provide a complete role-based user management for map.apps. Such a role-based user management means that any user can be assigned the role of a map.apps administrator (maAdmin) or editor (maEditor).
Role-based app protection with help from ArcGIS Online
An ArcGIS Online organization or ArcGIS Portal installation can be used as an alternative user administration for map.apps. In the standard configuration, an organization administrator is mapped to a map.apps administrator and an organizational Editor to a map.apps Editor.
Using secured maps or services
Content from ArcGIS Online
In map.apps, both protected and unprotected maps and services (Webmaps) can be integrated from ArcGIS Online. When a protected map is loaded in an app and accessed for the first time, a login dialog will appear where the user can enter his username and his password for ArcGIS Online. If the user does not have the appropriate rights, the app is started without the Webmap appearing; neither in the map nor in the content control. For more information, see [1].
Alternatively, the OAuth2 protocol for authentication to ArcGIS Online can be used. Here, when the user attempts to access a protected map, they are redirected to a login page on ArcGIS Online. After successful registration, the user is returned to map.apps and the App is displayed. In contrast to the direct integration of a protected Webmap in map.apps, in this case the application will not be displayed when the user is not able to log on successfully.
To use this OAuth authentication method, the map.apps App must be registered on ArcGIS Online as a webapp. In addition, some adjustments must be made, which are described in [1] under "OAuth".
Content from ArcGIS for Server
Analogous to the protected maps from ArcGIS Online, protected ArcGIS Server services can also be integrated into map.apps. When first accessing protected services, a login window will appear allowing the user to authenticate.
Managing users with map.apps User Managementmap.apps provides by default the two users, the "editor" and "administrator", for the management and configuration of apps in the map.apps Manager. If more users are working with the map.apps Manager, either the map.apps User Management Extension or security.manager is required. The map.apps User Management Extension adds an additional tab in the map.apps Manager, within which many users and user roles can be managed. In the background, a limited version of security.manager is used.
For the management and configuration of apps the User Management Extension provides the two roles "maAdministrator" and "maEditor", as with the map.apps core product.
Role-based configuration of Apps
In addition to the protection of map services, map.apps apps and app configurations can be extended, modified or restricted on a role-basis by means of map.apps User Management Extension or security.manager. For example, access to certain apps can be restricted to certain users., or access to specific funcitons, such as editing, can also be controlled to certain user roles.
Control of tools
Tools in map.apps are components with which certain functions can be turned on or triggered. Using a specific tool, for example, could result in a function being activated to select an area in the map. Another tool could open a print dialog. Tools therefore form the starting points for almost all advanced features. In order to limit certain functions of an application to a group of users, the so-called map.apps "Tool Rules" can be used. Among the many Tool Rules for other conditions, there are Tool Rules which can change tools, depending on the user role of the current user. A tool can be hidden, for example, or deactivated, so that it is no longer visible to the user or can no longer be activated. Here is an example of a Tool Rule, which pops up the print tool only if the user has the role of map.apps administrator maAdmin.
"toolrules": {
"ToolRuleManager": {
"_rules": {
"agsprinttool": {
"roles": ["maAdmin"],
"ruleSuccessProperty": "visibility"
}
}
}
}
In this example, the property "visibility" of the tool is switched. Further possible features are "active" to turn the tool on or off, and "enabled" in order to grey out the tool so that it cannot be clicked. In this way, all tools available in the app can be controlled and the functionality of an app easily limited.
Full app configuration manipulation
For further entitlements, the configuration of an app can be controlled with even finer granularity, but this requires that the file-based system is used, and not the map.apps Manager. With this method, it is possible to control each configuration attribute of any bundle component. In order to implement such a configuration, the central configuration file for an app, the app.json file, is given a "jsp" (Java Server Page) extension. The contents of this file is still the JSON description of the app configuration. As a JSP file, however, certain "tags" can be used which evaluate the server before delivering the app configuration to map.apps. These tags evaluate the role of the currently logged on user, and can then remove parts from the app configuration, add other parts or replace them.
The following example shows an excerpt from an app.jsp file. Here the bundle "selection" in the app is made available only if the current user has the role "sM_Administrator":
{
"load": {
"allowedBundles": [
"system",
"themes",
"windowmanager",
<s:isInRole role="sM_Administrator">"selection",</s:isInRole>
"authentication"
]
},
"bundles": {
...
}
Accordingly, the configuration of a component may also be finely adjusted. The JSP tag in this example determine that notifications to be displayed on a new position for the LocateMe bundle are only available to users with the role "sM_Administrator".
"locateme": {
"LocateMe": {
"showPositionLogs": <s:isInRole role ="sM_Administrator">true</s:isInRole>
<s:isNotInRole role ="sM_Administrator">false</s:isNotInRole>
}
}
For a more detailed description for setting up an app.jsp file, see [2] under "Role Based Functionality".
Additional security features with security.managerWith the User Management Extension, users and user roles can be managed. Moreover, to gain access to secured map services, to implement single sign-on scenarios or federations, security.manager is required. Even the printing of protected services is possible by means of security.manager.
Access control for map services
The securing of map services is the most common function of security.manager in interaction with map.apps. Here, security.manager is connected between map.apps and the underlying map services. map.apps then no longer engages directly with the with services to, but on the appropriate secured endpoints that are provided by security.manager. security.manager decides whether the access to a particular map resource is permitted or not. If access is allowed, security.manager passes the map request to the underlying map service and returns the result to the map.apps app (see figure).
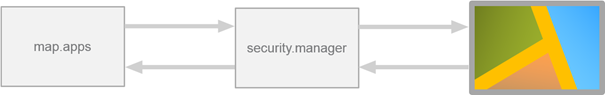
Filtering map service content
Unique to security.manager is the ability to impose fine-grained access control on spatial services. While most systems allow basic permit/deny access control, security.manager takes this further, providing a filtering mechanism that allows access to a service in general, while being able to filter content individually for different users. In this way, accessible content can be tuned per user, and can vary even within the same service. Spatial areas, individual layers, features and attributes can all be made accessible or hidden depending on the user’s role.
A classic example use case might be that of a service containing property information associated with a pipeline project. The pipeline company can access all layers, features and attributes of this map service. On the other hand, the service may contain sensitive private information that sub-contractors should not be able to access. By setting up an appropriate user role structure, contractor users may access the very same service, but may only see specific spatial areas relating to their work zone, may have a reduced set of layers available, appropriate to their work needs, and will not be able to see those attributes containing sensitive private information on land holders. By maintaining one service, and providing one service endpoint to apps, security.manager transparently controls the content delivered, based on the accessing user’s role and rights.
security.manager can either require authentication, or can provide unchallenged guest access to a service, in which case, appropriate access control policies, as defined by the security administrator, are still enforced. As the secured endpoints behave just like direct access service endpoints, no special customisation of the accessing client is needed.
Map services with user logon
For a closer integration of map.apps and security.manager, security.manager can be used as an authentication point. Users can log on within map.apps with their username and password. This data is sent to security.manager, checked and, of successful, access granted to the access to the map services. After authenticating the user, a domain cookie is set in the browser that is running in the map.apps and sent with each request to the server where it is used as identification.
To achieve such behavior, a further configuration of map.apps and security.manager is necessary. The SSO option is selected when choosing the authentication method for map services in security.manager. The service configuration in map.apps then differs from an unsecured configuration only in that it uses the SSO URL provided by security.manager as the URL to the required map service.
An example configuration for an SSO-protected service in map.apps looks like this:
{
"id":"secured_countries",
"type":"AGS_DYNAMIC",
"url":"https://myserver:443/wss/service/myAGS/sso/MyData/MapServer",
"layers":[{
"id":"3",
"title":"Countries
}]
}
Printing with security.manager and the ArcGIS for Server PrintTask
The printing of map services using the ArcGIS for Server PrintTask requires special settings when printing map services protected using security.manager.
Basic operation of ArcGIS for Server PrintTasks
To print a service using the PrintTask, the maps are not sent directly from map.apps to the PrintTask. Instead, map.apps communicates the required parameters to the PrintTask, such as the URLs of the desired map services and some additional information, such as to print a specific section of map, the scale, which map layers and their order. The PrintTask then runs with this information, sending the necessary requests to the map services and embedding the resultant map images in the print document. If the map services are protected by security.manager, it must be ensured that the PrintTask has access to this protected map services.
The following section describes how map.apps and security.manager must be configured to achieve this.
Configuration of the PrintTask for map.apps and security.manager
For all protected map services which are to be used for printing, the security.manager "agstoken" authentication method must be enabled. This is necessary so that the PrintTask can gain access to these services later. In addition, the PrintTask must be set up in security.manager as a geoprocessing service and the rights defined such that a user can address the map.apps PrintTask.
The URL that is provided by security.manager for the PrintTask must then be adjusted in the app configuration using the map.apps Manager. For this, the "url" property of the Printing Controller component in agsprinting bundle is set as in the following example:
"agsprinting": {
"PrintController": {
"url": "http://[...]/GPServer/Export%20Web%20Map"
}
Now when a PrintTask is called from map.apps that accesses a security.manager-protected map service, all URLs on the map services that have been notified to the PrintTask as a parameter are replaced with URLs on the agstoken-ATHN endpoints of the map services. In addition, the URLs are extended with a token-parameter containing the appropriate token for the for accessing user. With this token, access to the protected card services for the Print Task is then made possible.
Limitations
The printing of protected services using the PrintTask will only work if the map services are prepared on the same instance of security.manager as the endpoint for the PrintTask. The use of mapping services that are protected by another instance of security.manager as the PrintTask is not possible.
Functions matrix
map.apps
map.apps with User Management Extension
map.apps combined with security.manager
Authentication for ArcGIS Online contentApps protected against unauthorized access
Limited to Administrator and Editor
Fine-grained via user roles
Fine-grained via user roles
User role-based app configurations
![]()
![]()
![]()
User roles
Administrator and Editor
![]()
![]()
User number for app management
2 (Administrator and Editor)
Unlimited
Unlimited
User roles for app management
![]()
Administrator and Editor
Administrator and Editor
Single Sign-On und SAML 2
![]()
![]()
![]()
Federation
![]()
![]()
![]()
Protect Map Services
![]()
![]()
![]()
Additional Information (Login required)
[1] Documentation for setting up protected maps from ArcGIS Online
[2] Creating an app.jsp page for enhanced protection of app functions
